How Xss To

Cross Website Scripting Xss Software Program Assault Owasp Basis
A reflected xss (or additionally called a non-chronic xss assault) is a particular form of xss whose malicious script bounces off of another internet site to the sufferer’s browser. it is surpassed within the query, normally, inside the url. it makes exploitation as easy as tricking a consumer to how xss to click on on a hyperlink. A complete manual to move web page scripting (xss) assault, a way to save you it, and xss trying out. pass web page scripting (xss) is one of the maximum popular and inclined attacks which is known by way of each advanced tester. it's far taken into consideration as one of the riskiest assaults for the net programs and can deliver harmful results too. Saved cross-website online scripting. stored xss (additionally referred to as chronic or 2d-order xss) arises when an software receives facts from an untrusted source and consists of that information within its later http responses in an risky manner.. the facts in query might be submitted to the software thru http requests; as an instance, feedback on a blog submit, person nicknames in a chat room, or contact information on.
Cross-website scripting assaults (xss) can be used by attackers to undermine software security in lots of ways. it is most usually used to thieve consultation cookies, which permits the attacker to impersonate the victim. similarly to that, xss vulnerabilities had been used to create social networks worms, unfold malware, deface websites, and phish for credentials. Cross-website scripting (xss) attacks are a form of injection, wherein malicious scripts are injected into in any other case benign and depended on websites. xss assaults occur whilst an attacker uses a web software to send malicious code, commonly within the shape of a browser aspect script, to a exclusive give up user. Move how xss to site scripting (xss) is a commonplace assault vector that injects malicious code into a susceptible web application. xss differs from other web assault vectors (e. g. square injections), in that it does not without delay target the software itself. as an alternative, the customers of the internet utility are those at.
Modsecurity For Cwp Manage Webpanel Wiki
See more motion pictures for how to xss. To recognize how to prevent cross-web site scripting (xss), see the object entitled: “the way to prevent cross-site scripting (xss)“. resources of untrusted input it's far crucial which you do now not neglect capacity sources of untrusted input, as doing so can also suggest you neglect a capacity problem.
compliance how a huge rock found out a tesla xss vulnerability jeremy kirk • july 16, 2019 compliance sudden password pointers from nist mike wilson • july 15, 2019 ► compliance the way to protect ssh keys ► compliance building a framework for Relying on the capability and records processed by the susceptible software, xss vulnerabilities can pose a huge danger to the business. attackers ought to steal exclusive facts, perform unauthorized how xss to activities, and take over the entire internet sessions of the victim customers. Go-site scripting (xss) stays one of the maximum commonplace safety vulnerabilities presently found in net-packages. this article gives insight into how to test your programs for cross-website online scripting (xss) defects using both manual and automatic means. Move website online scripting prevention cheat sheet advent. this article presents a easy fine version for preventing xss using output escaping/encoding well. whilst there are a huge number of xss assault vectors, following some simple policies can absolutely protect against this extreme attack.
Five Practical Scenarios For Xss Attacks Pentestgear Com Weblog
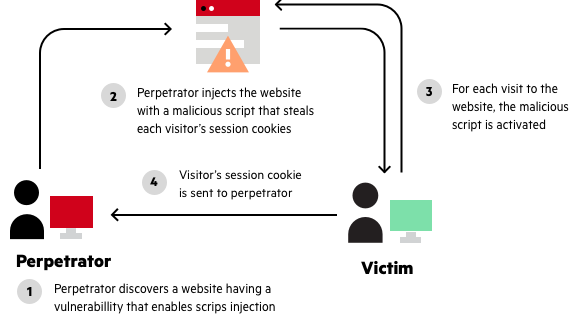
Relying at the functionality and records processed by way of the inclined utility, xss vulnerabilities can pose a good sized threat to the business. attackers should scouse borrow confidential statistics, perform unauthorized activities, and take over the entire net periods of the victim users. Xss locator (polygot) the subsequent is a “polygot test xss payload. ” this check will execute in more than one contexts together with html, script string, js and how xss to url. As it turns out, there are as a minimum two not unusual approaches of causing a victim to release a reflected xss assault in opposition to himself: if the user goals a specific individual, the attacker can send the malicious url to the victim (the usage of e-mail or if the person targets a big institution of humans, the attacker can. The actual xss attack is shaped by injecting unsanitised input into an internet application. the input is usually in the shape of javascript, that may be stored by the utility and again to different customers when they visit the web page. thereby executing the javascript within the customers browser.
Xss Educational Hackertarget Com

Cyber crimes watch cyber security, cyber crime, training, recognition.
the firewall can’t guard you from malware, xss and sq.-injection attacks modsecurity will assist to improve the safety of your server and scripts you're using on it how to fast discover from ssh which rule how xss to id Xss vulnerabilities are commonplace enough to have graced packages as large and famous as fb, google, and paypal, and xss has been a mainstay on the owasp top 10 listing on account that its inception. xss vulnerabilities are particularly risky because an attacker exploiting an xss attack can advantage the ability to do whatever the consumer can do, and to peer. might also 8, 2018 what is move-website scripting (xss) assault and the way to save you it muhammad haad ahmed june three, 2013
Go-site scripting (also known as xss) is one of the maximum not unusual application-layer web assaults. xss vulnerabilities target scripts embedded in a web page which might be accomplished on the purchaser-facet (in the person’s net browser) instead of at the server-aspect. development on this submit, we will take a look at how to permit server-facet caching in expressjs study on
redos vulnerabilities in npm spikes with the aid of 143% and xss continues to grow
snykio/ insecure wep utility please (oriwap) nancy snoke expertise xss christina mitchell social engineering at work a way to use tremendous affect to gain management purchase-in
Pass-web page scripting (xss) is a consumer-aspect code injection attack. the attacker targets to execute malicious scripts in a web browser of the victim by consisting of malicious code in a legitimate net web page or net software. the real attack happens when the sufferer visits the web web page or net software that executes the malicious code. Saved pass-web site scripting. stored xss (also known as chronic or 2nd-order xss) arises while an utility gets statistics from an untrusted supply and includes that records within its later http responses in an unsafe way.. the information in query is probably submitted to the software through http requests; as an example, remarks on a blog submit, person nicknames in a talk room, or touch info on. embedding in xml; it’s difficult to look how that api could do in any other case the launchpad integration code accordingly makes use of tal code along those traces, the use of the structure key-word to explicitly suggest that the excerpts in query do now not require html-escaping (like maximum top web frameworks, tal’s default is to break out all variable content, so a hit xss attacks on launchpad have traditionally been uncommon):
On this xss academic i'm able to provide an explanation for the fundamentals of pass web page scripting and the harm that could finished from an xss attack. many people deal with an xss vulnerability as a low to medium threat vulnerability, whilst in reality it's far a dangerous attack that could result in your users being compromised. Xss what is pass-website online scripting? pass-website scripting (additionally referred to as xss) is one of the maximum commonplace application-layer web assaults. xss vulnerabilities goal scripts embedded in a page that are executed at the consumer-facet (in the consumer’s internet browser) rather than on the server-facet. Go-website online scripting (xss) is a form of computer safety vulnerability generally located in net applications. xss attacks enable attackers to inject customer-side scripts into internet pages regarded with the aid of different users. a pass-website online scripting vulnerability may be utilized by attackers to skip get right of entry to controls together with the identical-origin policy. pass-web page scripting performed on web sites accounted for kind of eighty four%. Pass-site scripting (xss) assaults are a form of injection, in which malicious scripts are injected into otherwise benign and trusted websites. xss attacks occur whilst an attacker makes use of an internet application to ship malicious code, typically in the form of a browser facet script, to a exclusive quit consumer.
Komentar
Posting Komentar